More Ransomware targeting ESXI Hosts
More ransomware variants are seen on the wild targeting more and more ESXI hosts.
Within the few last months some ransomware variants have been found targeting ESXI servers and their virtual machines.
MalwareHunterTeam recently found a linux version of the REvil ransomware that was targeting ESXI servers by using the ESXCLI commands.
Today was detected a Blackmatter’s ransomware x64 linux variant \ ESXCLI Variant.
Firewall disable via ESXCLI:
esxcli network firewall set --enabled false
Forcibly Stop a Virtual Machine with ESXCLI
(query ..->”WorldID,DisplayName”):
esxcli vm process kill --type=force --world-id <ID>
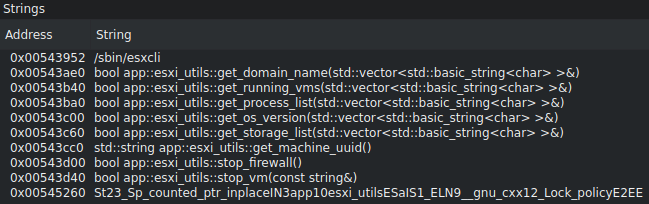
via: Vitali Kremez https://twitter.com/VK_Intel
https://twitter.com/VK_Intel/status/1423188690126266370
Crowdstrike has a really good article as well on ransomware targeting ESXI server:
https://www.crowdstrike.com/blog/carbon-spider-sprite-spider-target-esxi-servers-with-ransomware/
TrueSec has a really good post on Securing ESXI host against ransomware:
https://blog.truesec.com/2021/04/13/secure-your-vmware-esxi-hosts-against-ransomware/
Friendly reminder to have your ESXI host and vCenter management instances isolated and only accessible to the admins or persons in charge.
