A few days past, a particular Zero-Day vulnerability has been seen on the wild being exploited on pretty much ~ e v e r y t h i n g ~.
This Log4shell or Log4J is being tracked as CVE CVE-2021-44228 and it’s impact is pretty wide.
Why the broad impact?
Let’s try to define this Zero day, this vulnerability is based on the Java Logging library
You can imagine the rest when we say logging library and Java. Which is broadly utilized in big enterprise Java software tools.
Not only that but the amount of interdependencies and old tools using this log4j library makes the scope wider than many of the recent vulnerabilities out in the wild. Where definitely the number of vulnerable products will increase as time passes on.
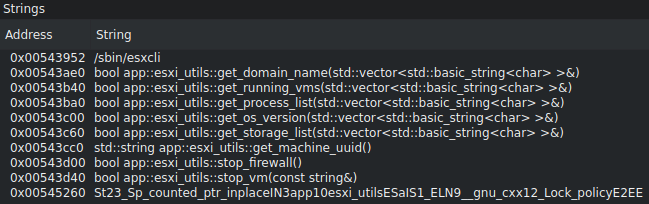
Some Hashes to help search for vulnerable Log4J versions:
https://github.com/mubix/CVE-2021-44228-Log4Shell-Hashes
You can find on the below github repo a Proof of Concept:
https://github.com/tangxiaofeng7/CVE-2021-44228-Apache-Log4j-Rce
and as well a nice Burp Suite extension useful to scan for log4j2rces :D
https://github.com/tangxiaofeng7/BurpLog4j2Scan

Randori has added details on VMware products impacted as well on below link:
https://www.randori.com/blog/cve-2021-44228/
Whereas VMware has released their Advisory with a list of impacted products:
https://www.vmware.com/security/advisories/VMSA-2021-0028.html
Under these all the most common solutions as vCenter Server, Horizon, NSX-T, Tanzu, among others.
Continue reading